At Revoxtech, we offer a suite of Identity Management Solutions that provide comprehensive protection across all access points, ensuring that the right individuals have the right access at the right time. Our solutions are tailored to meet the unique needs of businesses while maintaining the highest security standards.
Why Choose Revoxtech Identity Solutions?
Our Core Identity Solutions
At Revoxtech, we offer a comprehensive range of IAM solutions to manage user identities, secure access, and ensure compliance across your enterprise systems.
Application Onboarding
Streamlining Access to Applications
The process of application onboarding is a crucial aspect of managing access to your digital ecosystem. Revoxtech’s Identity Management Solutions simplify the onboarding process by providing:
- Pre-configured templates for rapid deployment, reducing setup time.
- Automation of user provisioning to minimize manual intervention and speed up access.
- Role-based access control (RBAC) to ensure users have the appropriate level of access based on their roles.
Seamless integration with various enterprise applications, including ERP, HR, and CRM systems, ensures that users can access the tools they need while maintaining security.
Benefits of Application Onboarding
- Reduced time and complexity of granting access.
- Centralized access control enhances security by reducing vulnerabilities.
- Improved user experience through quick and seamless onboarding.
- Minimized operational overhead with automated processes.
Access Management
Centralized Access Control and Monitoring
Access management is at the heart of identity security. Revoxtech’s solutions provide centralized control over who accesses what, when, and how. Key features include:
- Enforcement of uniform access policies across your organization.
- Real-time monitoring and logging of all access requests.
- Automated user role assignments based on predefined criteria.
- Fine-grained access control, enabling context-aware security for multi-device and multi-location access.
Key Benefits of Access Management
- Scalability to accommodate a growing user base.
- Secure access with the principle of least-privilege.
- Real-time visibility into user activity, reducing insider threats.
- Reduced risk of data breaches through robust access controls.
Cloud Infrastructure Entitlement Management
Protecting Cloud Resources
With the proliferation of cloud services, managing access across cloud environments is essential for cloud access control. Revoxtech’s solutions help you:
- Enforce access policies across AWS, Azure, GCP, and other cloud platforms.
- Manage entitlements and user permissions for various cloud services.
- Implement role-based and contextual access controls to safeguard cloud infrastructure.
- Automate entitlement reviews to minimize the risk of over-provisioned permissions.
Benefits of Cloud Infrastructure Entitlement Management
- Comprehensive audit trails for cloud access activity.
- Minimized security risks associated with excess privileges in the cloud.
- Simplified management of cloud entitlements.
- Support for multi-cloud environments, enhancing flexibility.
Customer Identity & Access Management (CIAM)
Secure and Seamless Customer Access
Providing secure, frictionless access to your customers is essential. Customer Identity & Access Management (CIAM) solutions from Revoxtech centralize customer identity and access across all platforms, offering:
- Support for multi-factor authentication (MFA) and SSO for secure and seamless customer access.
- Customization options to match authentication methods with your customer base.
- Compliance with global privacy regulations, including GDPR and CCPA.
- Streamlined registration and login processes, improving customer experience.
Key Benefits of CIAM
- Reduced friction during the onboarding and authentication process.
- Enhanced security with advanced authentication methods.
- Improved customer experience with easy-to-use access methods.
- Increased customer loyalty through secure, personalized experiences.

Identity Governance & Administration (IGA)
Simplifying Identity Lifecycle Management
Identity Governance & Administration (IGA) is essential for ensuring the security and compliance of user identities throughout their lifecycle. Key features of our IGA solutions include:
- Automated user provisioning and de-provisioning to ensure smooth transitions.
- Role-based and attribute-based access control (RBAC, ABAC) for fine-grained access management.
- Access certification and recertification to maintain compliance.
- Audit and reporting capabilities for compliance audits and risk assessments.
Benefits of Identity Governance & Administration
- Streamlined identity lifecycle management for efficiency and security.
- Ensured compliance with industry regulations and standards.
- Consistent identity policies across your organization.
- Reduced risks of unauthorized access and insider threats.
Identity Orchestrator (IO)
Automated Identity Workflows for Greater Efficiency
Revoxtech’s Identity Orchestrator (IO) centralizes and automates identity workflows, such as:
- Role assignments and policy enforcement.
- Automated access reviews to ensure continuous compliance.
- Self-service identity management for users to manage their profiles.
- Integration with HR systems, ERPs, and other enterprise applications.
Key Benefits of Identity Orchestrator
- Consistent identity processes across all business units.
- Increased operational efficiency by automating manual processes.
- Improved compliance with automated workflows.
- Enhanced user experience with self-service capabilities.
Privileged Access Management (PAM)
Secure and Control Access to Critical Systems
Managing privileged access is crucial for protecting critical systems. Our Privileged Access Management (PAM) solution allows you to:
- Protect privileged accounts and credentials with fine-grained control.
- Monitor and log privileged access sessions for audit and compliance purposes.
- Enforce least-privilege access to sensitive IT resources.
- Automate password management for privileged accounts.
Benefits of Privileged Access Management
- Detailed audit trails for monitoring privileged access.
- Reduced risk of privilege misuse and data breaches.
- Improved security with granular access control.
- Ensured compliance with internal and external standards.
Identity Management Solutions
Holistic Approach to Identity and Access Control
Our Identity Management Solutions provide a unified approach to manage user identities and access permissions across your organization. Features include:
- Centralized control over user identities and permissions.
- Adaptive security features, including MFA, SSO, and conditional access.
- Identity synchronization across on-premises, hybrid, and cloud environments.
- Advanced reporting and analytics for deeper insights into identity management.
Benefits of Comprehensive Identity Management
- Seamless access for authorized users to critical applications and data.
- Streamlined identity and access management across the enterprise.
- Enhanced security with centralized control over access policies.
- Regulatory compliance with consistent governance practices.
Cloud Access Control
Ensuring Security Across Cloud Environments
Revoxtech’s Cloud Access Control solutions ensure that your cloud resources are secure. We provide:
- Fine-grained access control for cloud platforms such as AWS, Azure, and GCP.
- Contextual access controls based on factors like location and device.
- Real-time monitoring and auditing of cloud access activity.
- Compliance with cloud security standards and best practices.
Benefits of Cloud Access Control
- Simplified cloud security posture management.
- Reduced risk of cloud data breaches.
- Better visibility into cloud user behavior with detailed reports.
- Centralized management of cloud and on-premises access.
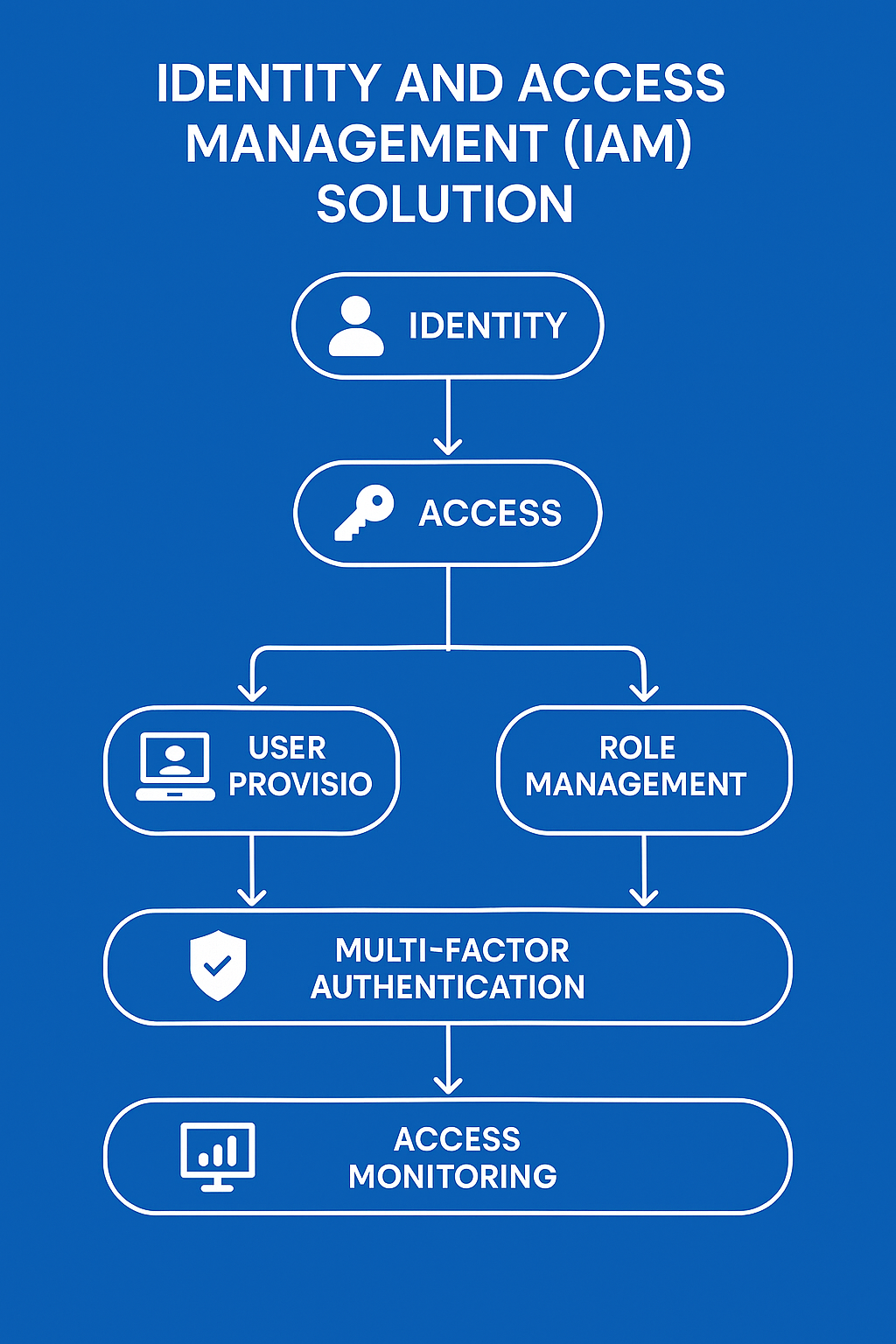
Identity and Access Management (IAM)
Comprehensive Identity and Access Management for Businesses
Revoxtech’s IAM solutions offer a comprehensive approach to securing user identities and controlling access. Our capabilities include:
- Identity verification, access control, and governance across all platforms.
- Support for hybrid and multi-cloud infrastructures.
- Customizable IAM systems to suit business-specific needs.
- Real-time monitoring and auditing to ensure access compliance.
Key Benefits of IAM Solutions
- Enhanced user satisfaction via seamless login experiences.
- Stronger security posture by controlling access to critical resources.
- Improved operational efficiency through IAM automation.
- Simplified user management across diverse platforms.
How Revoxtech Delivers Value
Would you like to start a project with us?
By choosing Revoxtech, you are investing in a secure, compliant, and efficient identity and access management solution that will safeguard your digital assets and enhance user experience. Let us help you navigate the complexities of IAM and secure your organization’s future.
